How much damage?
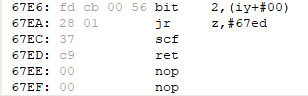
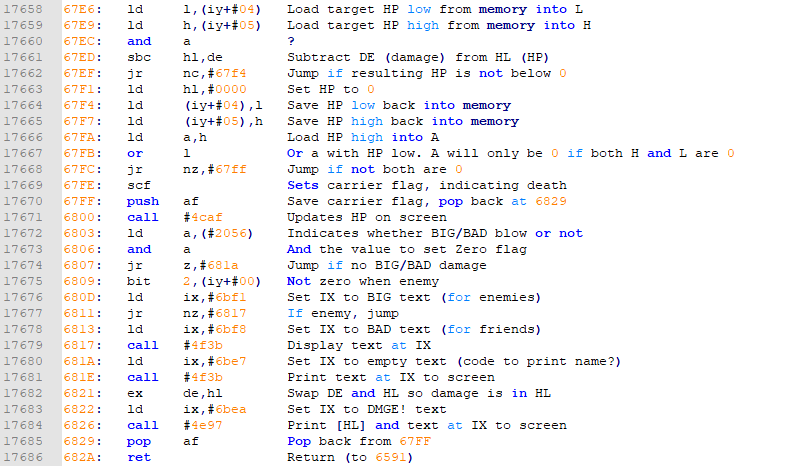
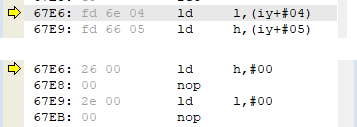
So in the previous post, we created our cheat to make us invincible. To make the cheat a little more sophisticated and show the damage done, we could write the instructions like in the following image. I will not explain what the code does. If you have read the previous posts, you must be able to figure this out yourself.
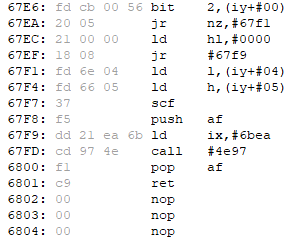
Way to get killed
Now we need a workaround for the fact that because we are unbeatable, the game is unfinishable. I have come up with one solution that can be developed inside the only method we have inspected so far. What if we kept track of a counter, which indicates the number of consecutive hits by an enemy on our party? That counter will increase every time we are hit, and when that counter reaches a certain number, our party members will become one hit kills as well. Then we could defend on each turn and let ourselves be hit until the counter reaches 10. We can reset the counter to 0 by hitting an enemy.
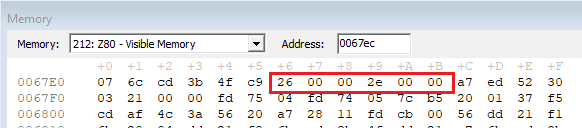
Now where can we store this counter? Since it needs to be persistent, we need to save it somewhere in memory. We have freed up the memory by simplifying the existing code, so I suggest to use the last free byte. This is on address #682a. We can load the value of this memory location into the A register and compare it with any number. So how can we compare?
To check whether a value is equal to another, we can use another bitwise operation, XOR. This checks each bit of both numbers, and is 1 if one of the two bits is 1, but only if the other one is 0. This is equivalent to the bit being 0 if both bits are the same. So the whole result of the XOR is only 0 if all bits are the same. So if we XOR two 8-bit numbers, the result is only 0 if those two numbers are the same.
Your new assignment is to alter the program so that:
- If we are hit by an enemy:
- No damage is done to us (we already implemented this).
- A counter is increased each time we are hit by an enemy.
- After 9 consecutive hits, we also become instant-death on each hit. So the 10th consecutive hit is the first deadly one.
- If we hit an enemy:
- The enemy is killed by doing damage equal to its HP (we already implemented this)
- The counter is reset to 0.
- Extra requirements
- The counter starts at 0.
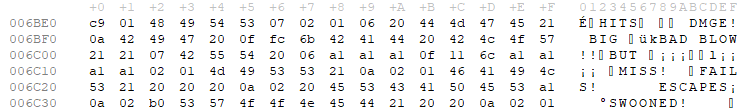
- When the counter is increased, the text ”[counter] OF 10″ is shown. We don’t show the 0 DMGE text anymore.
- When the counter is reset, the text “HITS RESET” is shown.
- When we or the enemy are killed in one hit, the text ”FATAL” is shown. We don’t show the DMGE text anymore.
I want you to try to develop this first for yourself. It is not that hard, and all the ingredients are know to you. Then read my solution.
My Solution
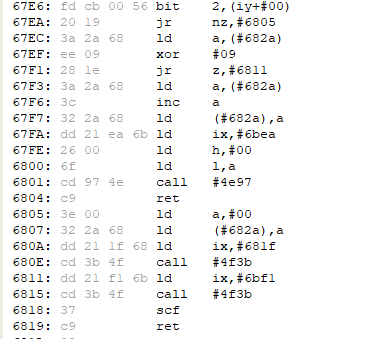
The code to implement the workaround is quite simple. The only thing to mention is the location of the text strings. In the old place, I removed the DMG! text, since we don’t need it anymore. I could not fit all the needed texts in here, I missed just one byte here. Since I had some bytes left empty because of the simplifying, I decided to put the text here.
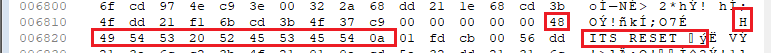
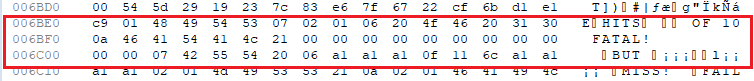
Changing the Disk File
Now that we have altered the game to make us invincible, we want to make this cheat available to others as well. We could just share our save game and tell them to load in into BlueMSX, but what if someone wants to play the cheated game on a different emulator or even a real MSX? This can be achieved by changing the original disk file. And we are in luck here! The parts of the memory that we have seen and changed is present on the disk. It is not encoded or encrypted in any way. Machine code files on disk are just memory dumps! So we can find our original code and change it. We need a HEX editor for that. I used HxD, but any HEX editor will suffice.
Now open the disk 1 file of the game in the HEX editor. Let’s look for the original code. The original method started with the values: FD 6E 04 FD 66 05 A7 ED 52 30 so let’s look for those. We need to search for the HEX values. We will find one entry, at #88E6. So now type all the codes for your new code. Also don’t forget the altered texts to display on the screen.
So for my solution, from #88E6, I entered: FD CB 00 56 28 04 DD 21 07 6C CD 3B 4F C9 FD CB 00 56 20 19 3A 2A 68 EE 09 28 1E 3A 2A 68 3C 32 2A 68 DD 21 EA 6B 26 00 6F CD 97 4E C9 3E 00 32 2A 68 DD 21 1F 68 CD 3B 4F DD 21 F1 6B CD 3B 4F 37 C9 00 00 00 00 00 48 49 54 53 20 52 45 53 45 54 0A. The last value is on 8929. So you can select the values in the HEX editor and paste the new values. And from #8CEA to #8D01, I entered the following values for the other texts: 20 4F 46 20 31 30 0A 46 41 54 41 4C 21 00 00 00 00 00 00 00 00 00 00 00.
Now we can save the disk file and open it in BlueMSX. Restart the machine and start the game. You will see the altered code is there! So we have created a cheated version of the game for the world to enjoy!
Also the start stats of the characters are in the disk file. I want you to find the stats on the disk (they will be like the memory from #2300) and cheat the game even more by setting the starting experience very high. By defeating one enemy, I want Selios to level up all the way to lvl99. Also, I want the game to start with max gold.
I have included a cheated .dsk file so you can see it work.